Spotlight on Ransomware: How ransomware works

Understanding how ransomware works is no easy task. Outside of cyber security circles, grasping the complexities required to protect and prevent ransomware from harming its victims can seem almost impossible. This only makes the threat all the scarier and effective for the criminals that stand to profit.
In Emsisoft’s ‘Spotlight on Ransomware’ series, we aim to break down the different stages of a ransomware attack, from infection vectors and malware execution to encryption and ransom payment mechanics.
If you missed Part One, ‘Common ransomware infection methods’, be sure to check that out and learn about the various ways ransomware is spread.
In Part Two, we will explore what happens once you’ve made that unfortunate click on a link or document, and what the ransomware does to your system to take control.
Ready to find out how ransomware works? Let’s dive in.
How ransomware works: Gaining access rights
With thousands of different ransomware variants out there and growing by the day, explaining the precise steps of how ransomware works to take over a system vary across different strains. In general, once ransomware is executed it wastes no time scanning local and connected drives for files to encrypt.
Expert tip: Since many ransomware variants will try to encrypt connected and shared drives, it is critical to keep external hard drives disconnected from your computer when you aren’t making backups. If they are attached when you’re being attacked it will most likely be encrypted as well.
Some variants such as Locky and DMA Locker can even encrypt unmapped network shares, making the proliferation of the infection even more widespread.
All of this happens in a matter of seconds. Literally.
Yet a lot happens in these seconds, so let’s take a look at some of the different ways ransomware seeks to take over your computer.
Obfuscation and process injection
When delivered to your system, ransomware is usually packed by some kind of obfuscator or packer. Much like with spoken language, obfuscation uses ambiguous and confusing expressions to compose statements that conceal the actual intended meaning.
But what does that look like in the context of software?
Firstly, ransomware developers will obfuscate code to conceal its purpose. Take anti-malware software for example: If ransomware runs exactly as it was written it should trigger your security software and block that action. But what if your system thinks you are running a typical windows program?
This is ransomware’s objective of obfuscation: to remain undetected.
Secondly, malware often gets reverse-engineered by security researchers to extract the code, figure out how it works and then create a decrypter to unlock the ransomware. If the source code has been obfuscated, this becomes a much more difficult task. If a security researcher is looking at jibberish code it can be near to impossible to determine what the source code ever looked like.
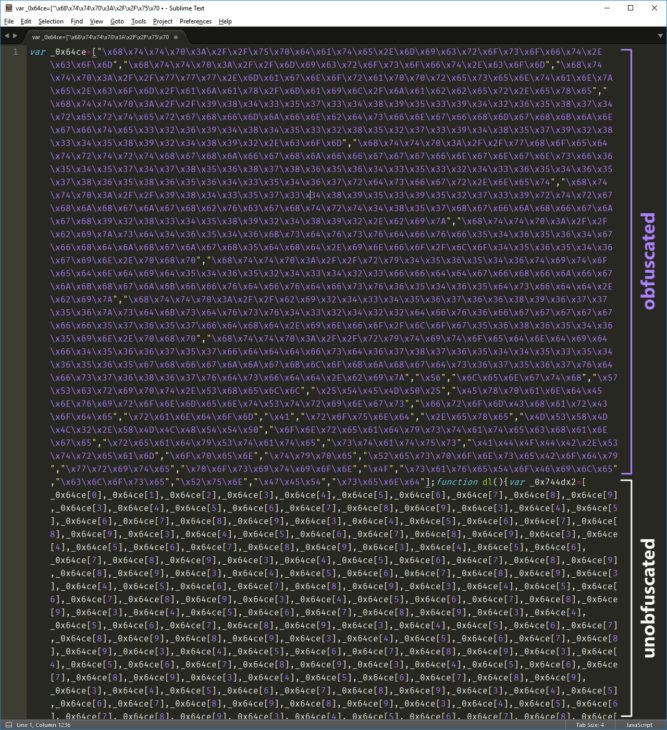
obfuscated v unobfuscated source code
This method is made even easier by the use of automatic obfuscation software. This software automatically changes the file data in various ways so it doesn’t look much like the original. however, the file can still execute perfectly fine.
Quick definition: Obfuscation is a process by which the ransomware changes file data in various ways so it doesn’t look like the original source code. This conceals the true purpose of the file while still allowing the file to execute.
Once the obfuscated file has started to run in your system, the ransomware will unpack itself into the memory.
Since obfuscators can be applied multiple times in many layers, unpacking may even happen repeatedly, depending on the configurations used. One way this unpacking works is through code injection done into a newly created process.
UAC bypass
User account control (UAC) is a security measure that Microsoft originally introduced with Windows Vista. Based on ‘the principle of least privilege,’ Windows by default limits all applications on your computer to standard user privileges. If an application requests higher privileges, you will see the below pop-up appearing on your computer, requiring a user with admin rights to confirm in order to continue.
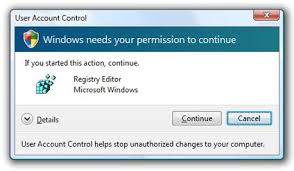
UAC pop-up notification
This is the scary part of how ransomware works in this particular scenario: With UAC bypass, ransomware can stop this popup from ever appearing. With UAC bypass ransomware operates at higher privileges allowing it to make changes to your system and interact with other programs without you even realizing.
But how does it do this exactly?
Let’s look at Erebus ransomware as an example:
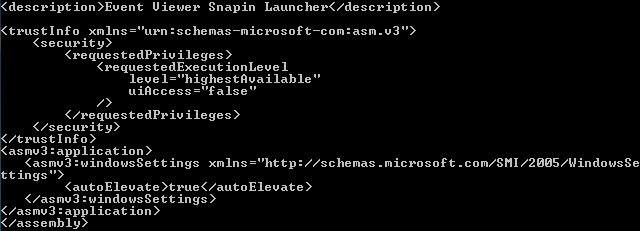
As explored in depth by Matt Nelsen, Erebus copies itself to a randomly named file in the same folder as the UAC. Then, it modifies the Windows registry in order to hijack the association for the .msc file extension. This basically means that it will launch the random name Erebus executed file (.exe) instead of prompting the UAC permissions popup.
Erebus tricks your computer into opening the Erebus file at the highest permissions level on your computer. This means that it all happens in the background without alerting you or asking you to approve the application launch.
As Event Viewer runs in the same elevated mode (admin level), the launched Erebus executable file (.exe) will also launch with the same privileges. This allows it to bypass User Account Control completely.
Quick definition: User Account Control (UAC) bypass is a process by which malware can elevate its own privileges to admin level without your approval, allowing it to make changes to your system such as encrypting all of your files.
But how does a UAC bypass avoid detection?
While ransomware using process injection attempts to avoid detection through the use of obfuscation technology, the latest UAC bypass technique differs in its approach. Security researcher Matt Nelson explains how on his blog and summarized below:
- Most (if not all) previous UAC bypass techniques required dropping a file (typically a Dynamic-Link Library, or, DLL) to the file system. Doing this increases the risk of an attacker being caught either in the act or later when an infected system is investigated – particularly if their source code is not obfuscated as explained above. Since the UAC bypass technique doesn’t drop a traditional file, that extra risk to the attacker is mitigated.
- This UAC Bypass technique does not require any process injection such as the typical obfuscation and process injection technique. This means the attack won’t get flagged by security solutions that monitor for this type of behavior. (Note: Emsisoft solutions do monitor for this type of behavior. You can learn more about our behavior blocker technology here.)
Basically, this method significantly reduces the risk to the attacker because they can gain admin rights without having to risk the user saying no. Whilst the principle of a UAC bypass isn’t new, it has been gaining traction and is now a common feature for a ransomware to include. Two examples of malware which have used this are the Erebus ransomware (discussed above) and the Dridex Banking Trojan, have adopted this method and have been circulating since early 2017.
Establishing persistence: Ransomware makes itself comfortable
Occasionally ransomware will attempt to stay in your system as long as possible by creating what is called persistence. This makes sure that the ransomware will stay on the system, continues to encrypt new files as they are copied and even infect new victims by spreading to other drives.
There are a many different ways ransomware can achieve persistence. Below we are highlighting the most common ones:
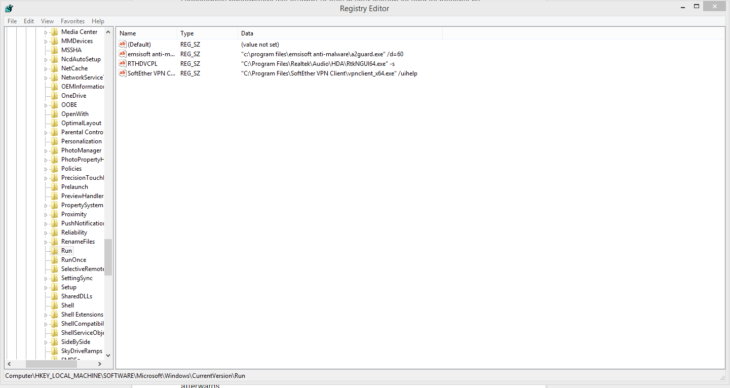
Planting run keys
Run keys are located in the registry so every time a user logs on, programs which are listed there are being executed. These do not run in safe mode unless prefixed by an asterisk, meaning that the program will run in both normal and safe mode. If you have persistent ransomware that seems to just keep coming back again over and over no matter how many times you think you’ve killed it, this could be your problem.
One such example is the Javascript RAA ransomware, which appeared in 2016.
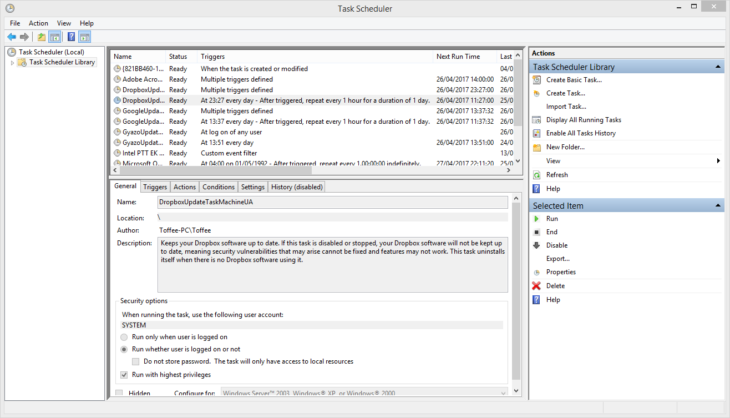
Scheduling a task
Scheduled tasks are another method we have seen ransomware use, allowing for more flexibility of when a program should run. For example, you can set a program to run every 30 minutes, meaning your see the same malware at startup and every 30 minutes afterwards. Some variants of ransomware, such as CTB Locker or CryLocker, are known to employ this technique.
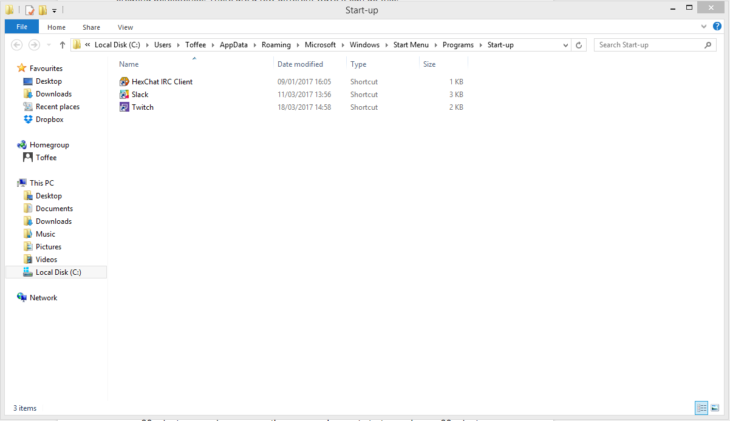
Embedding a shortcut
If a shortcut to the malware file or copy of the malware file is located in the startup folder, it will be run when the computer boots.
A more sophisticated use of shortcuts has recently been observed in ransomware such as Spora. Borrowing the characteristics of a worm, the ransomware will set the ‘hidden’ attribute to files and folders in the root of all drives. It will then create shortcuts (.lnk) with the same names as the hidden ones and delete the associated arrow symbol in the registry that usually indicate a shortcut icon. The shortcut itself will contain the arguments to open the original file or folder as well as the ransomware file, ensuring the system continues to remain unusable until it is disinfected.
Command & control servers: Calling home
We have seen how ransomware works its way into your system. Once the ransomware has established a firm hold, most of them will communicate with a command and control server (also known as C2) from your computer for a variety of purposes.
Usually they will either use hard-coded domains or IP addresses, but can also be hosted on hacked websites. Take Nemucod ransomware for example. This malware family hacks websites, adds a folder to the FTP (usually named counter), and uses that site as the website to host not only the malware that gets downloaded to infect victims (drops their own weak ransomware, and the Kovter banking Trojan typically), but also hosts the “payment portal”, where the victim then goes to get the decrypter if they chose to pay.
Alternatively, a domain generation algorithm (DGA) is employed. A DGA is a piece of code in the ransomware that will generate and contact numerous domains. The malware author will know in which order these domains are likely to be generated and pick one of them to register. The advantage of DGA over hard-coded domains is that it makes it difficult to take down all the domains at once so there is often somewhere for the ransomware and the ransom payment pages to be hosted.
Once the connection is established, the ransomware can send information about your system to the server, including;
- the operating system you use,
- your computer name,
- your user name,
- the country in which you are located,
- your user ID,
- a generated bitcoin address,
- the encryption key (if it is generated by the malware).
Conversely, the C2 server may send information back to the ransomware, such as the server generated encryption key to use to encrypt your files, a generated bitcoin address where you will be asked to pay the ransom, a user ID to access the portal and the payment site URL (Note: we will cover this aspect in an upcoming post in this series).
In some cases, the C2 may also instruct the ransomware to download other malware once it has finished encrypting or to make copies of your files to be used to blackmail you for more money in the future.
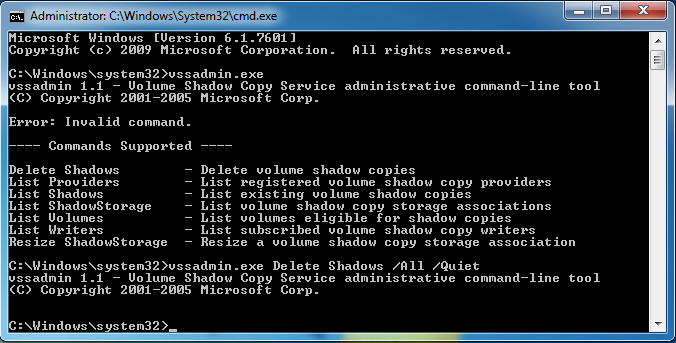
Removing shadow copies: No turning back(up)
The final stage in a ransomware’s takeover of your system before encryption begins is typically the removal of any shadow copies (or automatic backup copies) of your files. This prevents the victims from reverting back to the unencrypted versions and avoiding to pay the ransom.
Volume Shadow Copy Service (VSS), which was originally included in Windows XP Security Pack 2, is a set of interfaces that can be set to automatically create “backups” of files, even when they are in use.
These backups are usually created when a Windows Backup or System Restore point is created. They allow you to restore files to previous versions.
This is something ransomware does not want.
This results in ransomware usually deleting the snapshots using the command vssadmin.exe Delete Shadows /All /Quiet, and it will do so without any prompts warning the user. To do this, it needs administrator permissions and is another reason why ransomware would want to use a UAC bypass.
Conclusion
As you can see, there are various ways that ransomware takes hold of your system and all kinds of changes that it can make to render it unusable. From gaining admin rights or bypassing them altogether, establishing persistence by changing registry entries and setting up shortcuts, to communication with a command and control server: how ransomware works is getting more sophisticated by the day.
Now that you understand how ransomware invades your system, get ready to dive into the next step of the attack: encryption of your files. Stay tuned for the next post in our series in the coming weeks!
Many thanks to EMSIsoft AntiMalware software for this article. Contact SWC for your Emsisoft products.