
Following the emergence of the Jaff ransomware attack campaign earlier this week, another, even bigger outbreak is making headlines. The culprit? A new ransomware family called WannaCry or WCry.
Spotted earlier today, WCry caught the attention of the team due to it being spread via the recently exposed NSA shadow broker exploits. WCry took many businesses and public institutions by surprise, including telco giant Telefonica in Spain and the National Health Service in the United Kingdom, and has already infected tens of thousands of systems across the globe.
Security researcher MalwareTech created a map of overall infections and a real time map of infections to visualise the number of WCry infections, which has surpassed the 350,000 infection mark across more than 100 countries worldwide.
Meet WannaCry Ransomware
The WCry ransomware, also referred to as WNCry, WannaCry, WanaCrypt0r or Wana Decrypt0r, was originally spotted in campaigns in early February 2017, with more campaigns following in March. But it wasn’t until now that a global attack had been registered.
It has been written in C++ and no attempts have been made to hide the majority of the code. Like most ransomware families, WCry renames files it encrypts, adding the .WNCRY extension.
When infecting a system, it presents a ransom screen asking to pay $300 worth of bitcoins:
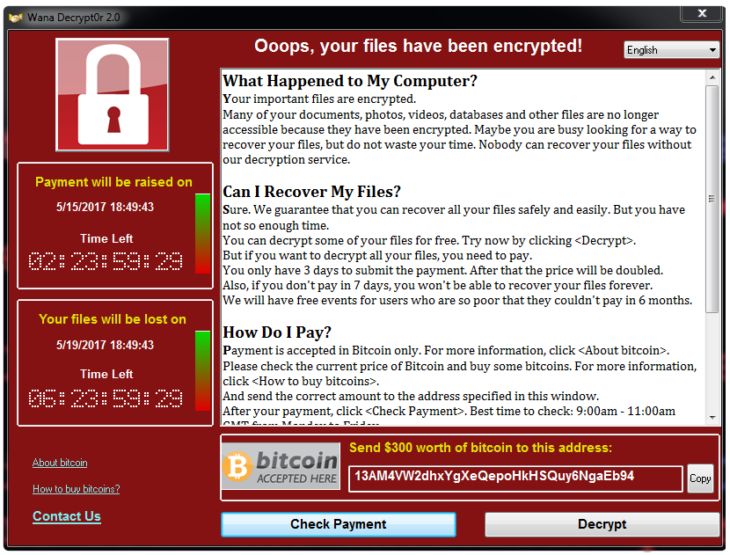
Unlike most ransomware campaigns, which usually target specific regions, WCry is targeting systems around the globe. So it comes as no surprise that the ransomware authors provide localised ransomware message for more than 20 languages:
Bulgarian, Chinese (simplified), Chinese (traditional), Croatian, Czech, Danish, Dutch, English, Filipino, Finnish, French, German, Greek, Indonesian, Italian, Japanese, Korean, Latvian, Norwegian, Polish, Portuguese, Romanian, Russian, Slovak, Spanish, Swedish, Turkish, Vietnamese
How do you get infected with WCry ransomware?
At the moment, WCry is primarily spreading via the leaked NSA exploits that the Shadow Brokers group released recently. More specifically, French researcher Kaffine was the first to suspect that WCry was being spread via the ETERNALBLUE exploit.
ETERNALBLUE exploits a vulnerability in the Microsoft SMBv1 protocol, allowing an attacker to take control over systems which:
- have the SMBv1 protocol enabled
- are accessible from the internet and
- have not been patched by the MS17-010 fix released back in March 2017
In addition, it appears that the malware authors are also taking advantage of DOUBLESPEAR, a backdoor that is usually installed via the ETERNALBLUE exploit and persisting on the system. So if your system was compromised by ETERNALBLUE previously, chances are your system is still vulnerable, even if the initial SMBv1 vulnerability was patched.
The ransomware executable itself can be best described as a dropper that contains all the different ransomware components in form of a password protected ZIP archive within its file. When run, it will start unpacking its components to the directory it was executed in using the hardcoded password “WNcry@2ol7”. Closer inspection of the ZIP archive reveals the following files:
- b.wnry – Ransom desktop wallpaper
- c.wnry – Configuration file containing C2 server addresses, BitCoin Wallet etc.
- r.wnry – Ransom note
- s.wnry – ZIP archive containing the TOR client
- t.wnry – The encryption part of the ransomware encrypted using a WanaCry specific format; can be decrypted using the private key embedded inside the ransomware executable.
- u.wnry – Decrypter executable
- Taskdl.exe – Deletes all temporary files created during encryption (.WNCRYT)
- Taskse.exe – Runs given program in all user sessions
- msg\* – Language files (currently 28 different languages)
In addition the ransomware creates a couple of additional files during its execution:
- 00000000.eky – Encryption key for the t.wnry file which stores the actual file encryption component used by the ransomware. It is encrypted using the public key that belongs to a private key embedded inside the ransomware.
- 00000000.pky – Public key used by the ransomware to encrypt the generated AES keys that are used to encrypt the user’s files
- 00000000.res – Command & Control Server (C2) communication results
A list of all changes made by the ransomware to an infected system, can be found in the “Indicators of Compromise” section below.
WCry key generation and encryption
WCry ransomware uses a combination of RSA and AES-128-CBC to encrypt the victim’s data. To facilitate this process, is uses the Windows CryptoAPI for RSA, but a custom implementation for the AES encryption.
Interestingly, the encryption routine is stored in a separate component within the t.wnry file, and is itself encrypted using the same method used by the ransomware to encrypt user files. This was likely done to make the malware analysis more difficult. The module is loaded into memory using a custom loader and executed from there, without ever being written to the victim’s disk unencrypted.
When WCry arrives on a system, it will first import a hardcoded private RSA key that is used to decrypt the file encryption component stored within “t.wnry”. Once done, the ransomware will generate a new private RSA key. That RSA key is then submitted to the malware’s command and control server and a copy of the generated public key is stored on the system.
The ransomware then searches all available drives and network shares for files with one of the following extensions:
.der, .pfx, .key, .crt, .csr, .p12, .pem, .odt, .ott, .sxw, .stw, .uot, .3ds, .max, .3dm, .ods, .ots, .sxc, .stc, .dif, .slk, .wb2, .odp, .otp, .sxd, .std, .uop, .odg, .otg, .sxm, .mml, .lay, .lay6, .asc, .sqlite3, .sqlitedb, .sql, .accdb, .mdb, .db, .dbf, .odb, .frm, .myd, .myi, .ibd, .mdf, .ldf, .sln, .suo, .cs, .cpp, .pas, .asm, .js, .cmd, .bat, .ps1, .vbs, .vb, .pl, .dip, .dch, .sch, .brd, .jsp, .php, .asp, .rb, .java, .jar, .class, .sh, .mp3, .wav, .swf, .fla, .wmv, .mpg, .vob, .mpeg, .asf, .avi, .mov, .mp4, .3gp, .mkv, .3g2, .flv, .wma, .mid, .m3u, .m4u, .djvu, .svg, .ai, .psd, .nef, .tiff, .tif, .cgm, .raw, .gif, .png, .bmp, .jpg, .jpeg, .vcd, .iso, .backup, .zip, .rar, .7z, .gz, .tgz, .tar, .bak, .tbk, .bz2, .PAQ, .ARC, .aes, .gpg, .vmx, .vmdk, .vdi, .sldm, .sldx, .sti, .sxi, .602, .hwp, .snt, .onetoc2, .dwg, .pdf, .wk1, .wks, .123, .rtf, .csv, .txt, .vsdx, .vsd, .edb, .eml, .msg, .ost, .pst, .potm, .potx, .ppam, .ppsx, .ppsm, .pps, .pot, .pptm, .pptx, .ppt, .xltm, .xltx, .xlc, .xlm, .xlt, .xlw, .xlsb, .xlsm, .xlsx, .xls, .dotx, .dotm, .dot, .docm, .docb, .docx, .doc, .c, .h
Once done, the malware will generate a new 128 bit AES key for every file it found, which is encrypted using the public RSA key generated earlier and the RSA-encrypted AES key is stored within the header of the encrypted file, together with the file marker “WANACRY!”. The AES key is then used to encrypt the file’s content.
Unfortunately, after evaluating the way WCry performs its encryption, there is no way to restore encrypted files without access to the private key generated by the ransomware. So it’s not likely a free WCry ransomware decrypter will be available for victims.
How can I protect myself from WannaCry?
As an emergency measure, make sure to have the latest security updates installed on your Windows computers and servers. Given the scale of the attack, Microsoft even took the unusual step to release security patches for “unsupported systems” such as Windows XP and Windows Server 2003.
As explained in our ransomware article, the best protection still remains a reliable and proven backup strategy, especially since the encryption used by WCry ransomware is secure. The only way to get the data back is through the help of the ransomware author or via restoring from backups. Making sure to install critical windows updates is also a very important step in protecting a system, as WCry only seems to be spreading via the SMBv1 exploit currently, which has been patched for 2 months already.
Apart from regular backups, you will be glad to hear that the Behavior Blocker technology used by Emsisoft Anti-Malware and Emsisoft Internet Security has proven to be the next best defense, as it has caught the ransomware before the file could execute and thus once again keeping our users protected from this and hundreds of other ransomware families without the need for signatures. Contact SWC for your Emsisoft products.
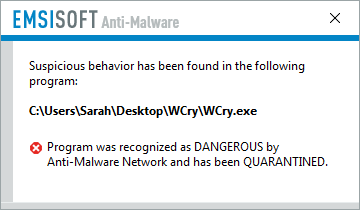
Emsisoft Anti-Malware and Emsisoft Internet Security users are protected from WCry by our Behavior Blocker
We consider ransomware one of the biggest threats of the past year and plan to do our best to continue our excellent track record in the next year, to keep our users as protected as possible.
It seems to be an impossible puzzle yet it’s easy to solve the Rubik’ Cube using algorithms.
Indicators of Compromise
Registry:
- HKLM\SOFTWARE\WanaCrypt0r
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\<random>: “”<ransomware directory>\tasksche.exe””
- HKLM\SOFTWARE\WanaCrypt0r\wd: “<ransomware directory>”
- HKU\S-1-5-21-677641349-3533616285-3951951702-1000\Control Panel\Desktop\Wallpaper: “{e9cb1494a64698e9f88d6af7d495ed8f3c3af9743680b5bc421a8ae007be863b}APPDATA{e9cb1494a64698e9f88d6af7d495ed8f3c3af9743680b5bc421a8ae007be863b}\Microsoft\Windows\Themes\TranscodedWallpaper.jpg”
- HKU\S-1-5-21-677641349-3533616285-3951951702-1000\Control Panel\Desktop\Wallpaper: “<ransomware directory>\@[email protected]”
File system:
- @[email protected] – Placed inside every folder that contains encrypted files
- @[email protected] – Placed inside every folder that contains encrypted files
- {e9cb1494a64698e9f88d6af7d495ed8f3c3af9743680b5bc421a8ae007be863b}DESKTOP{e9cb1494a64698e9f88d6af7d495ed8f3c3af9743680b5bc421a8ae007be863b}\@[email protected]
- {e9cb1494a64698e9f88d6af7d495ed8f3c3af9743680b5bc421a8ae007be863b}DESKTOP{e9cb1494a64698e9f88d6af7d495ed8f3c3af9743680b5bc421a8ae007be863b}\@[email protected]
- {e9cb1494a64698e9f88d6af7d495ed8f3c3af9743680b5bc421a8ae007be863b}APPDATA{e9cb1494a64698e9f88d6af7d495ed8f3c3af9743680b5bc421a8ae007be863b}\tor\cached-certs
- {e9cb1494a64698e9f88d6af7d495ed8f3c3af9743680b5bc421a8ae007be863b}APPDATA{e9cb1494a64698e9f88d6af7d495ed8f3c3af9743680b5bc421a8ae007be863b}\tor\cached-microdesc-consensus
- {e9cb1494a64698e9f88d6af7d495ed8f3c3af9743680b5bc421a8ae007be863b}APPDATA{e9cb1494a64698e9f88d6af7d495ed8f3c3af9743680b5bc421a8ae007be863b}\tor\cached-microdescs.new
- {e9cb1494a64698e9f88d6af7d495ed8f3c3af9743680b5bc421a8ae007be863b}APPDATA{e9cb1494a64698e9f88d6af7d495ed8f3c3af9743680b5bc421a8ae007be863b}\tor\lock
- {e9cb1494a64698e9f88d6af7d495ed8f3c3af9743680b5bc421a8ae007be863b}APPDATA{e9cb1494a64698e9f88d6af7d495ed8f3c3af9743680b5bc421a8ae007be863b}\tor\state
- <ransomware directory>\00000000.eky
- <ransomware directory>\00000000.pky
- <ransomware directory>\00000000.res
- <ransomware directory>\@[email protected]
- <ransomware directory>\@[email protected]
- <ransomware directory>\b.wnry
- <ransomware directory>\c.wnry
- <ransomware directory>\f.wnry
- <ransomware directory>\msg\m_bulgarian.wnry
- <ransomware directory>\msg\m_chinese (simplified).wnry
- <ransomware directory>\msg\m_chinese (traditional).wnry
- <ransomware directory>\msg\m_croatian.wnry
- <ransomware directory>\msg\m_czech.wnry
- <ransomware directory>\msg\m_danish.wnry
- <ransomware directory>\msg\m_dutch.wnry
- <ransomware directory>\msg\m_english.wnry
- <ransomware directory>\msg\m_filipino.wnry
- <ransomware directory>\msg\m_finnish.wnry
- <ransomware directory>\msg\m_french.wnry
- <ransomware directory>\msg\m_german.wnry
- <ransomware directory>\msg\m_greek.wnry
- <ransomware directory>\msg\m_indonesian.wnry
- <ransomware directory>\msg\m_italian.wnry
- <ransomware directory>\msg\m_japanese.wnry
- <ransomware directory>\msg\m_korean.wnry
- <ransomware directory>\msg\m_latvian.wnry
- <ransomware directory>\msg\m_norwegian.wnry
- <ransomware directory>\msg\m_polish.wnry
- <ransomware directory>\msg\m_portuguese.wnry
- <ransomware directory>\msg\m_romanian.wnry
- <ransomware directory>\msg\m_russian.wnry
- <ransomware directory>\msg\m_slovak.wnry
- <ransomware directory>\msg\m_spanish.wnry
- <ransomware directory>\msg\m_swedish.wnry
- <ransomware directory>\msg\m_turkish.wnry
- <ransomware directory>\msg\m_vietnamese.wnry
- <ransomware directory>\r.wnry
- <ransomware directory>\s.wnry
- <ransomware directory>\t.wnry
- <ransomware directory>\TaskData\Tor\libeay32.dll
- <ransomware directory>\TaskData\Tor\libevent-2-0-5.dll
- <ransomware directory>\TaskData\Tor\libevent_core-2-0-5.dll
- <ransomware directory>\TaskData\Tor\libevent_extra-2-0-5.dll
- <ransomware directory>\TaskData\Tor\libgcc_s_sjlj-1.dll
- <ransomware directory>\TaskData\Tor\libssp-0.dll
- <ransomware directory>\TaskData\Tor\ssleay32.dll
- <ransomware directory>\TaskData\Tor\taskhsvc.exe
- <ransomware directory>\TaskData\Tor\tor.exe
- <ransomware directory>\TaskData\Tor\zlib1.dll
- <ransomware directory>\taskdl.exe
- <ransomware directory>\taskse.exe
- <ransomware directory>\u.wnry
- C:\@[email protected]